2019/02/18 @ QuoScient Medium
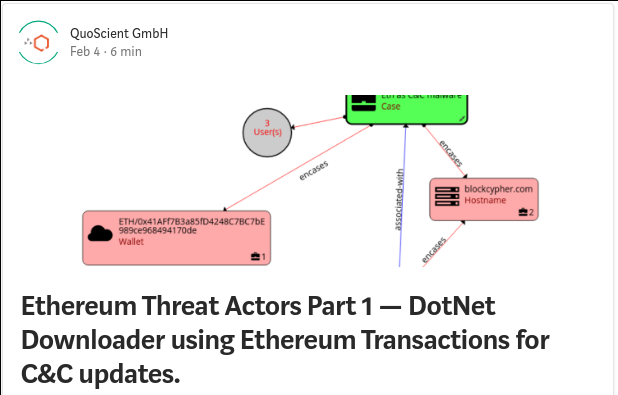
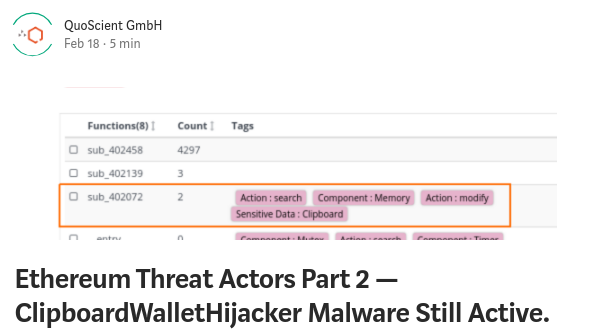
In part two of our mini-series (see part #1) describing how cybercrime actors are using the Ethereum blockchain for fraudulent means, we analyze a clipboard hijacker malware targeting Bitcoin and Ethereum users. This malware, renamed ClipboardWalletHijacker by Qihoo360 Security Center, was first discovered in June 2018, after having infected 300 thousand computers within a week.
- Quick ClipboardWalletHijacker Analysis
- Hijacked Ethereum Transactions
- Cryptocurrency Exchange Used by the Actor
- Packers & Variants
- Conclusion
- Indicator of Compromise