2019/04/03 @ QuoScient Medium
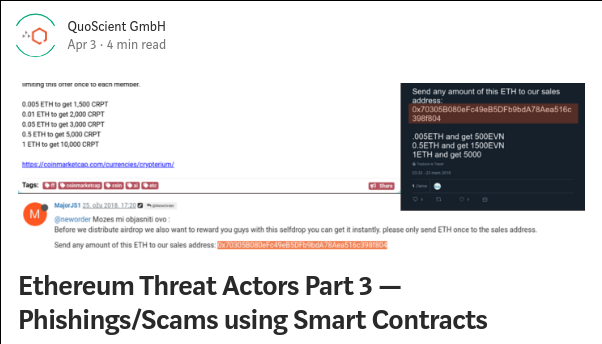
In part three of our mini-series (see part #1 & part #2) describing how cybercrime actors are using the Ethereum blockchain for fraudulent means, we analyze a phishing tactic that used a smart contract address. Interestingly, this smart contract is not unique and the exact same closed-source bytecode is used in more than 130 thousand smart contracts.
- Phishing on Forums/Telegram.
- Quick analysis of the Smart contract Bytecode
- Who is behind 0xAf1931c20ee0c11BEA17A41BfBbAd299B2763bc0?
- Similar Luno user wallets Used for Phishing
- Conclusion
- Indicator of Compromise
