2018/11/08 @ BlackAlps 2018
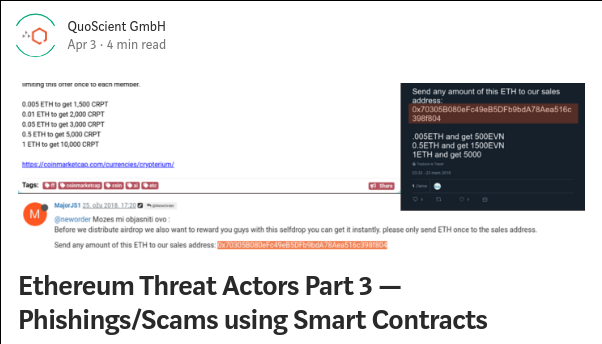
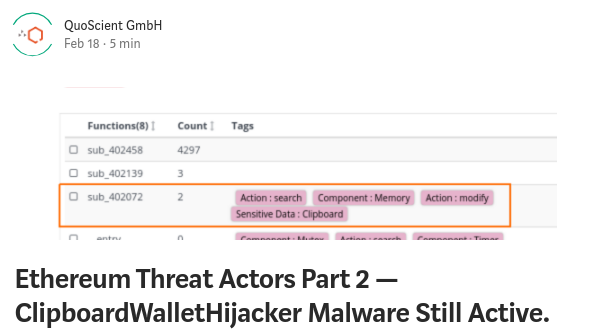
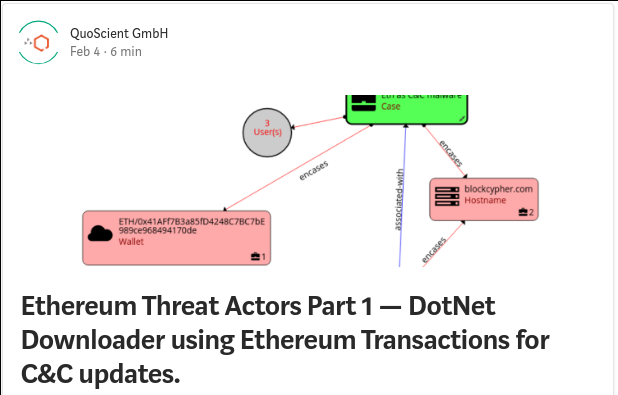
Ethereum is the reference of smart contract platform due to the possibility to create decentralized applications (Dapps) by writing smart contracts. The Solidity source code of those smart contracts are not always available and can contains flaws (reentrancy, integer overflow/underflow, bad randomness, backdoor, ….). Some smart contract handle thousand of ETH and can’t be modified once pushed into the blockchain. More than 90% of them doesn’t provide the associated Solidity source code and that’s also why be able to reverse and analyze Ethereum smart contract (only with the EVM bytecode) make even more sense.
This workshop is intended to bring attendees the basic skills (theoretical and practical) to analyze Ethereum smart contracts. After the workshop, they will be able to reverse, debug and find basic vulnerabilities into real-life smart contracts without having the Solidity source code.
The following points will be covered in the workshop:
- Quick introduction of Ethereum
- Basic Ethereum testing lab
- Reverse engineering of Ethereum smart contracts
- Analysis and vulnerability research
- Going deeper & Questions
link / slides / video