2019/02/04 @ QuoScient Medium
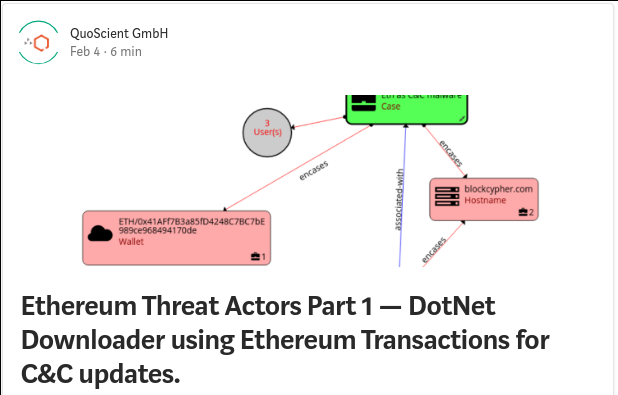
As part of our research into how cybercrime actors using the Ethereum blockchain for fraudulent means, we analyzed a DotNet downloader that retrieves the malicious payload from URLs stored inside Ethereum transactions. We analyzed the sample provided by a German Security Researcher, Karsten Hahn @struppigel in this tweet.
- Downloader analysis
- Main Function
- GetLastTransactionHashFromAddress function
- GetAdditionalDataFromTransaction function
- Transaction analysis
- C&C Update Pricing
- Blockcypher service
- Future of Ethereum botnet
- Conclusion
- Indicators of Compromise
