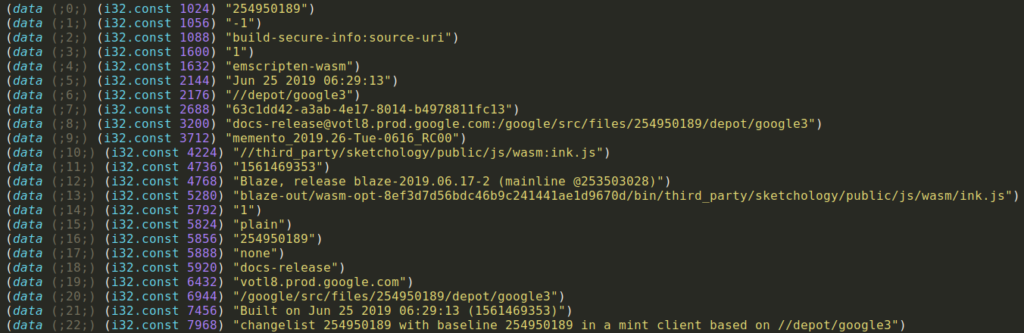
2018/09/15 @ ToorCon XX – 2018
WebAssembly (WASM) is a new binary format currently developed and supported by all major browsers including Firefox, Chrome, WebKit /Safari and Microsoft Edge through the W3C. This new format have been designed to be “Efficient and fast“, “Debuggable“ and “Safe” that why it is often called as the “game changer for the web“. More than one year after the “official” release, it is not only used “for the web” by web browsers but also in some (huge) other projects like Blockchain Smart Contract platforms (EOS and Ethereum).
I will first introduce WebAssembly concepts and who currently used it in the wild. Secondly, I will show different WebAssembly VM available and explain the security measures implemented into it. Finally, I will show you, throw real life WASM modules, how to do static analysis, using techniques such as reversing, control flow and calls flow analysis, to understand deeper its behaviors. Along the talk, I will used multiple open source tools but mainly the one that I have developed and that is already available on Github (Octopus).
link / slides / video