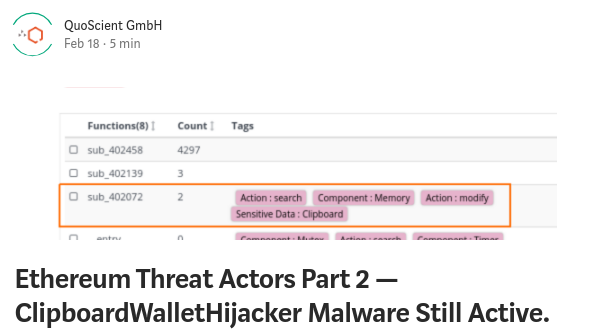
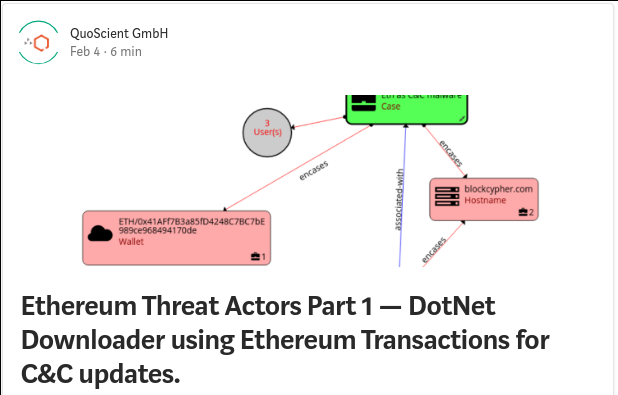
2019/02/18 @ EthCC 2019
At Devcon4, Vitalik annonced that WebAssembly (wasm) will be part of Ethereum 2.0 (Serenity). It’s already possible to compile smart contracts to wasm modules and run them in the Kovan network.
Using WebAssembly smart contract doesn’t mean using secure smart contract.
In this talk, I will explain what’s inside a WebAssembly module and illustrate how to analyze wasm Ethereum smart contracts to find vulnerabilities and unoptimization.
- Introduction
- WebAssembly basics
- Program analysis
- Parity Helloworld
- WASM module Vulnerabilities
- Conclusion