2020/03/03 @ EthCC 2020
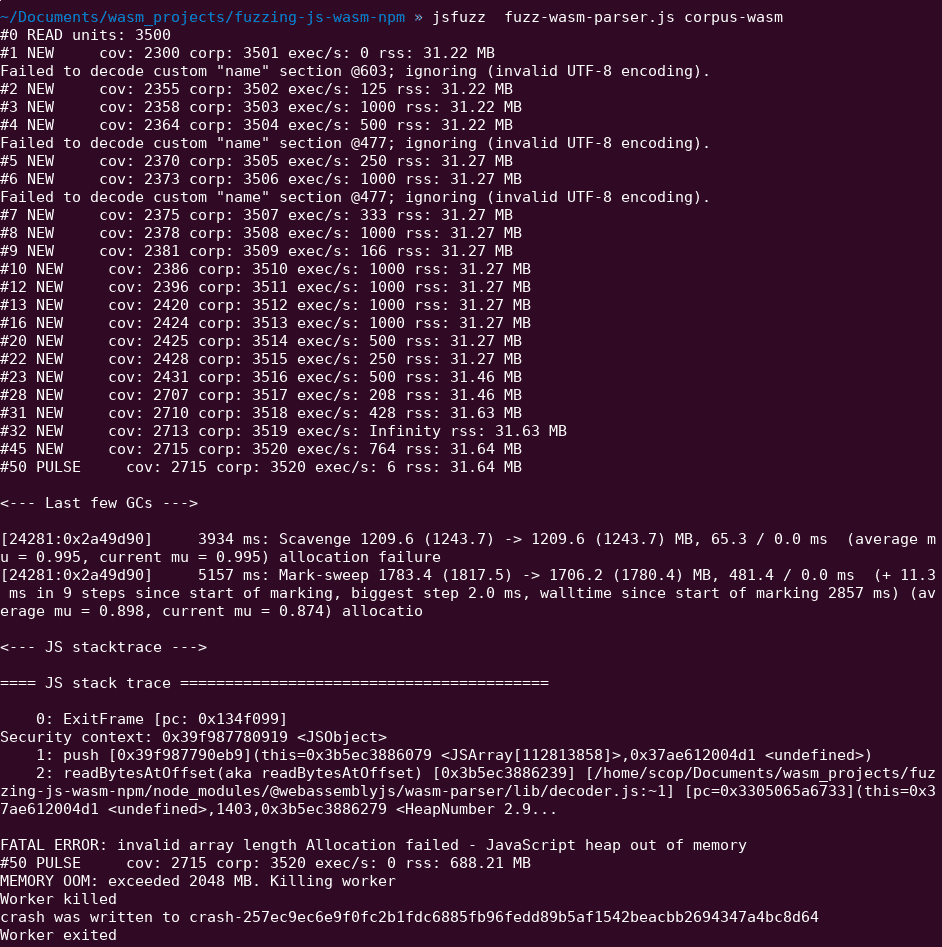
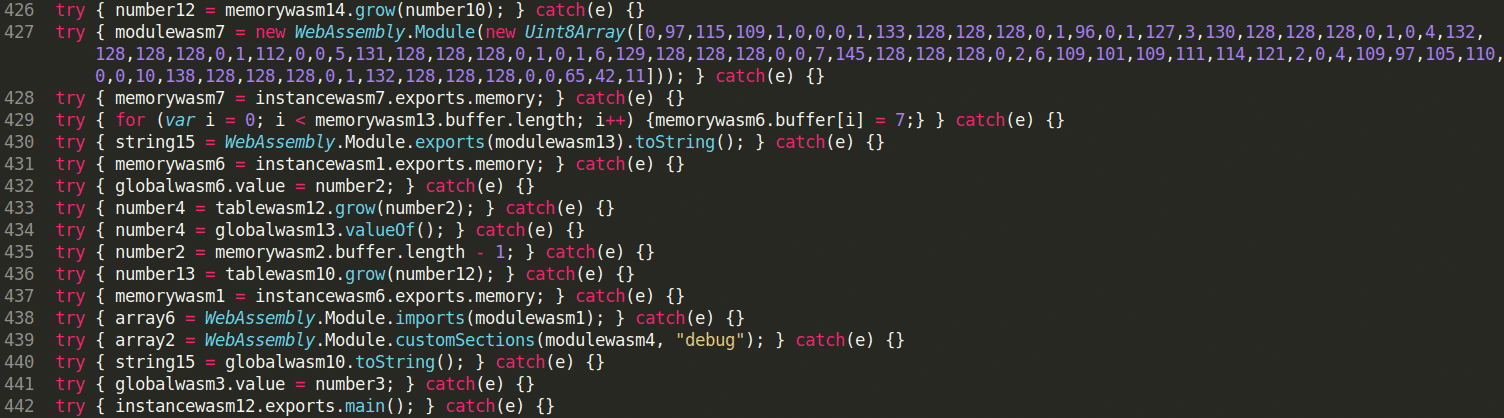
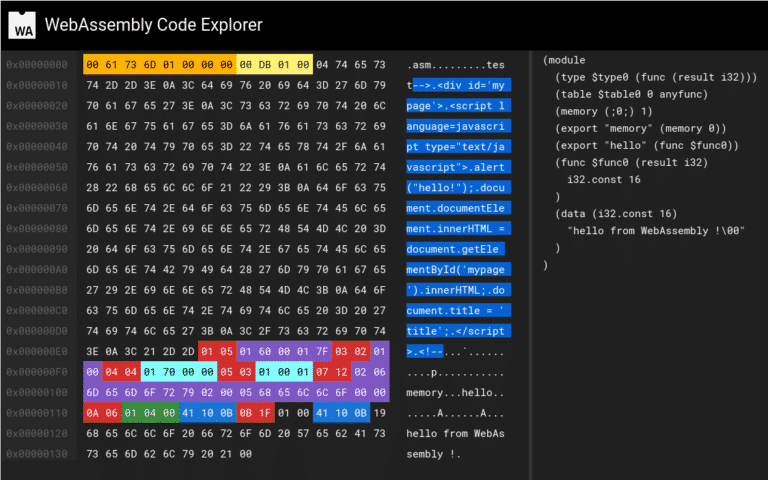
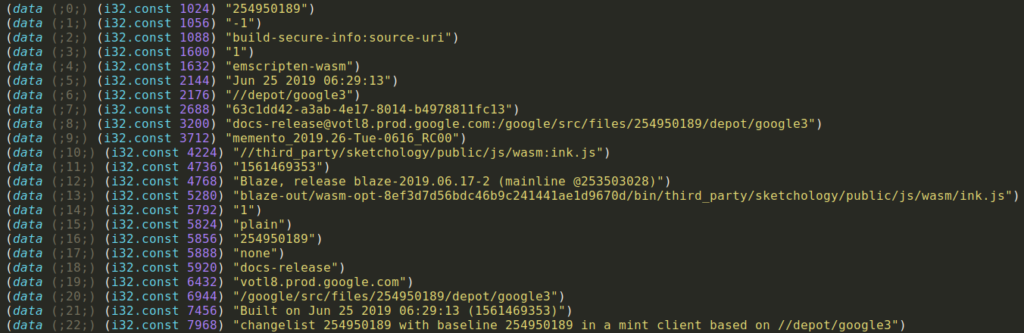
In this talk, I briefly introduce WebAssembly concepts , Ewasm specificity and opcodes/instructions. Secondly, I show how to create Ewasm smart contract and expose different techniques/tools to perform WebAssembly module closed-source analysis. Finally, we go through some basic examples to apply reversing (reverse engineering) on those Ewasm contracts and understand the logic inside.